Reposted with permission from Hartford Business Journal.
In the two years since Connecticut lawmakers created some legal protections for businesses that adopt accepted cybersecurity standards, companies large and small have worked to boost their computer and network security, experts said.
The legislation, which went into effect in October 2021, protects businesses from punitive damages in the case of a data breach where personal or restricted information is accessed, as long as companies have adopted and adhered to appropriate cybersecurity measures.
Businesses and other organizations have sought to make their networks impenetrable to hackers — not only to prevent cyber attackers from gaining access, but also to protect themselves from potential litigation if individuals’ private information is accessed, experts said.

Ashley Zane, a lobbyist with the Connecticut Business & Industry Association, said her organization has seen a “huge focus on cybersecurity” following the law’s passage.
The manufacturing industry in particular has been looking to improve cybersecurity, especially businesses that are suppliers to major Connecticut defense companies, like Sikorsky and Electric Boat, Zane said.
“There’s been a huge focus on those small to midsize companies to upgrade their cybersecurity, because one way for a cybercriminal to get at a Sikorsky or a Pratt & Whitney is through one of the smaller companies,” Zane said.
Punitive damages
The Federal Bureau of Investigation’s Internet Crime Complaint Center received 800,944 complaints last year, with cybercrime losses exceeding $10.3 billion, according to the FBI’s 2022 Internet Crime Report.

Chris Wisneski, manager of IT security and assurance services with accounting and consulting firm Whittlesey, said he’s seen a “huge increase” since the 2021 law’s passage of businesses seeking to improve their cybersecurity to meet industry-recognized standards.
It ranges from credit unions to nonprofits and schools, from very small businesses to large ones, he said. His firm recently helped a nonprofit with just four employees and a law firm with two.
“We’re seeing all size organizations just really pick up on this and realize this is a must, that they have to do this,” Wisneski said. “By (lawmakers) putting that law in place, it has certainly prompted companies to take cybersecurity a little more seriously, especially with the protection from punitive damages.”
Michael Grande, president and CEO of Vancord, a Milford-based cybersecurity services provider, said the law has prompted businesses to make cyber upgrades.
For many organizations, however, the biggest motivator for making cybersecurity enhancements has been related to their ability to obtain cyber liability insurance, as carriers often insist on a security program, Grande said.
The incentive of securing lower premiums has also been a factor, he added.

Sherwin M. Yoder, an attorney who leads the privacy and data security practice at law firm Carmody Torrance Sandak & Hennessey, said he’s seen more interest from businesses calling his firm about cybersecurity.
According to Yoder, the 2021 law protects only against potential punitive damages, and a business or entity could still face having to pay compensatory damages because of litigation filed following a cyber attack.
Even so, Yoder said he expects proper compliance with a recognized cybersecurity framework “will minimize the scope and severity of harms that might flow from a security breach.”
“Protecting businesses against punitive damages — that’s still a significant protection,” Yoder said.
Breaches and lawsuits
Hackers have been successful recently attacking multiple Connecticut targets, from large hospitals to a city.
California-based Prospect Medical Holdings, which owns Waterbury, Manchester Memorial and Rockville General hospitals, was the victim of a ransomware attack reported in early August.
While Prospect indicated its clinical staff has continued to provide uninterrupted patient care, it had to take computer systems offline.
In another recent breach, about $6 million was stolen from the New Haven school system after a hacker got access to a city worker’s email account and was able to secure wire transfers. The city, as of August, had recovered about $3.6 million.
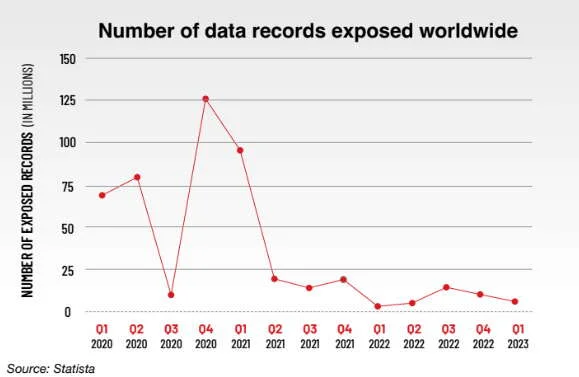
According to Statista, in the first quarter of 2023 alone, more than 6 million data records were exposed via breaches worldwide.
Meanwhile, the number of lawsuits related to cyber attacks continues to grow.
On Aug. 17, a class action lawsuit was filed in U.S. District Court in Connecticut against Hartford Life and Accident Insurance Co. claiming it failed to properly safeguard personal information, from names and dates of birth to Social Security numbers.
The litigation claims cybercriminals infiltrated the Hartford-based insurance company’s “inadequately protected” network servers in a data breach in May.
A federal class action lawsuit filed in May against Stamford-based Webster Bank claimed nearly 200,000 customers’ personal information was exposed because of a data breach, putting them at risk for identity theft and fraud.
In March, a federal class action was filed in Connecticut against Ridgefield-based Merritt Healthcare Advisors over a data breach discovered in November 2022. Plaintiffs claim the business failed to safeguard their personal information and failed to notify them until March 2023.
Nationwide, class action cases related to cyber attacks have been filed in recent months against Johns Hopkins University, Norton Healthcare in Kentucky, and the law firm Orrick, Herrington & Sutcliffe International, to name a few.
‘Just nonstop’
Wisneski, of Whittlesey, in late August was working on seven open cyber breach cases for clients, and he described the frequency of breaches as “just nonstop.”
Cyber attackers are most frequently using tactics such as phishing, in which a hacker pretends to be someone trustworthy, typically via email, to gain sensitive data like bank account information.
A new trend has been “multifactor bypass.” Through typical multifactor authentication, many entities require not just a password, but a secondary step, such as a code sent via text that a user has to enter.
Now, hackers are setting it up so it appears to a user that they are doing this secondary authentication, when actually the hackers are stealing their session, according to Wisneski.
“We rely on multifactor and think it’s got to be secure, well now you can’t think like that all the time, unfortunately, because of this new attack,” Wisneski said.
Another common ploy used by hackers is to target third-party vendors or suppliers to larger entities, such as banks. Those secondary targets may have much of the information hackers want, while being easier to infiltrate.
Steve Maresca, a senior security engineer at Vancord, said ransomware is the “biggest threat that most businesses see on their horizon.”
“The chief concern that keeps everyone up at night is ransomware — the disabling of data and services because it’s encrypted by an attacker,” Maresca said.